
In order to provide cloud solutions to government agencies, it was necessary to comply with cloud procurement guidelines such as ISO/IEC 27017 and NIST SP 800-171, security guidelines set by the US government. One of the challenges was to strengthen the management of privileged accounts. At the time, manual management using Excel and other tools was not sufficient to meet the requirements of "NIST SP 800-171." The company considered using internal resources, but in order to focus on developing internal services, it was decided to consider a solution that could manage privileged access as a package.
CyberArk centrally manages privileged access to the in-house development environment, enhancing security.
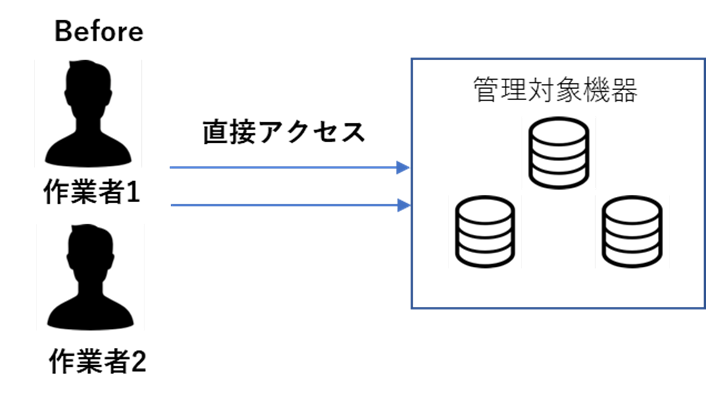
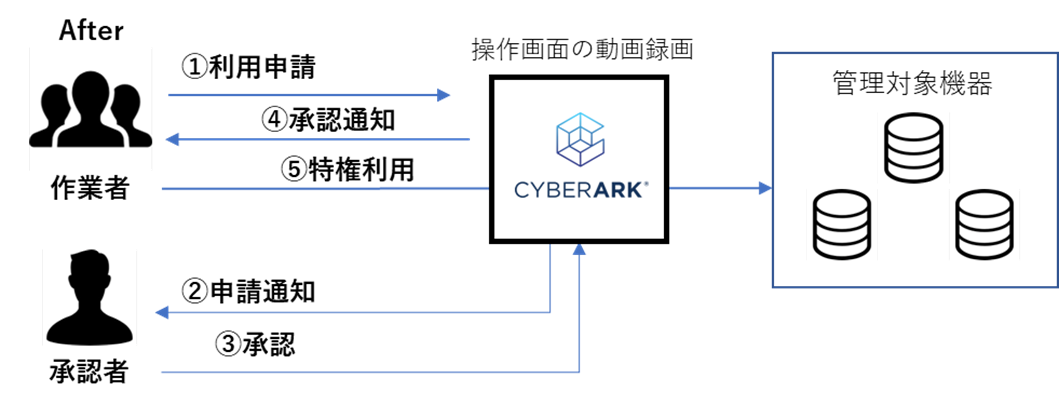
CyberArk privilege management was applied to all environmental access related to the services provided. The environment that had been operated based on the user's good intentions was corrected, and information leakage countermeasures, such as password confidentiality, were strengthened. In addition, CyberArk introduced an application approval flow for privileged access, recorded operation logs, and monitored activities so that the logs could be used for auditing purposes. Security related to privileged access has been strengthened. Security certification based on ISO/IEC27017 was obtained.
CyberArk privilege management was applied to all environment access related to the services provided. The environment, which had been operated based on the user's good intentions, was corrected, and information leakage countermeasures, such as password confidentiality, were strengthened. In addition, CyberArk introduced an application approval flow for privileged access, recorded operation logs, and monitored activities so that the logs could be used for auditing purposes. D55 has acquired security certification based on ISO/IEC27017.