
A security policy was formulated that required all group offices to comply with the management of privileged IDs, and it was imperative that domestic offices also comply with the policy. However, the current operation was not able to meet the requirements for privileged ID application and log management of privileged user activity, etc. In order to meet the requirements, the company began considering the introduction of CyberArk.
CyberArk implements privileged ID management function to enhance privileged access security
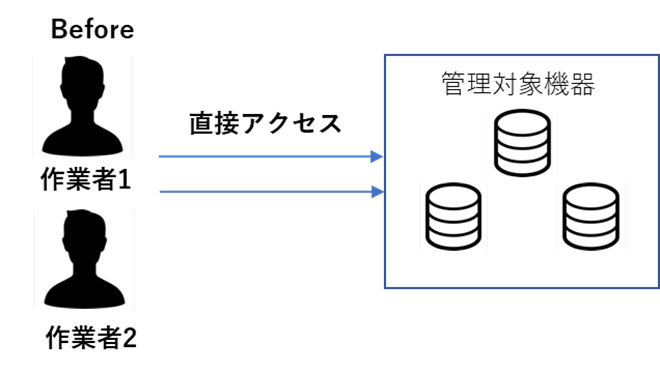
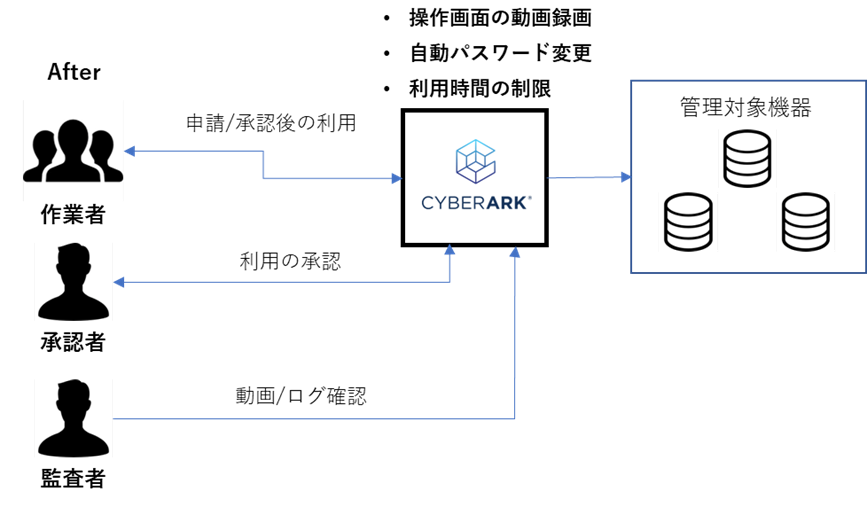
Unified operation using a workflow for application approval and simplified auditing work by recording and saving videos and logs of work using privileged IDs. Also, as a requirement for use, privileged IDs can only be used at specific times, enhancing operational security in associated with the use of privileged IDs. Operation in accordance with the group's security policy has been achieved.
When the application approval workflow was introduced, user operations required to change, but we were able to create and deploy internal rules to proceed the changes that accompanied with the achievement of security requirements without disruption. Since application credential management is possible with CyberArk, we will consider to implement it in the future.