SERVICE
Privileged Account Management and Protection
"Privileged account management and protection" is one of the most important countermeasures against Advanced Persistent Threat and Internal Fraudulent Acts. Managing privileged accounts is significantly important for criteria of various security guidelines such as SOX Act, PCI DSS, NIST SP800-171, System Management Standards (METI), as well as for internal control audit. While attacks and unauthorized access against companies are increasing rapidly, the scope of privileged access management keeps expanding, and strong security that is not limited to manage like before is required. We provide implementation and operational support for CyberArk, which has established a proven track record on a global scale, to help you strengthen the security of privileged accounts.
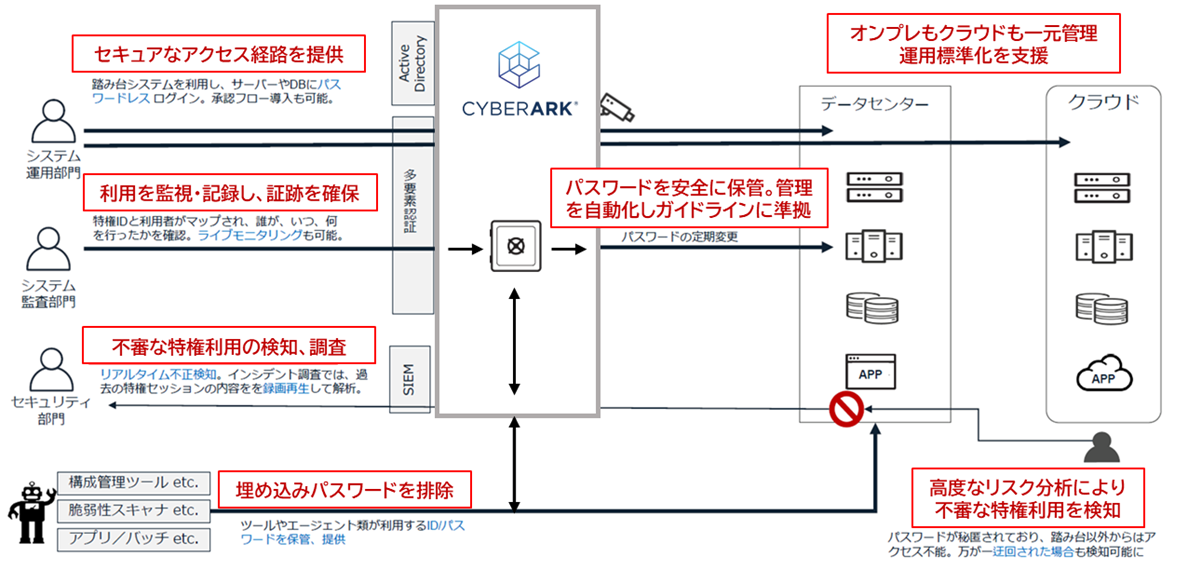
CyberArk solves complicated management situations that could lead to privileged information leakage.


CyberArk manages privileged access to the systems centrally.
The feature of CyberArk is not distributing passwords but storing it only in CyberArk. Also, log in to the system, controls user access, records access and activities, and changes passwords automatically.
The privileged passwords are hidden from users, and the privileged information will not remain on user or work terminals by logging in using multi-factor authentication.
Application
Please contact us to let us know the services you are interested in. Your request will be reviewed and a proposal from implementation to operations will be prepared. The contract will be proceeded if there is no problem with the content.
Preparation for the project
Our requests for the implementation of the system will be presented, and there will be action items required by clients after signing of the contract.
In addition to project management, from requirement definition to construction including testing will be provided as a construction support.
Once the implementation support starts, from requirement definition to detailed design, construction, and testing will be provided in order to integrate with the customer's system. Operational support will be provided after the implementation of CyberArk is complete.
| Requirement definition (implementation support) | ・Hearings on the usage and management status of privileged accounts to determine whether CyberArk can manage them |
|---|---|
| Design and construction (Implementation support) | ・Implementing the design of infrastructure and CyberArk software in accordance with requirements. |
| Testing (Implementation support) | ・Confirmation of the system operating as expected |
| Explanation for administrators/users (Introduction support) | ・Training of necessary tasks for administrators/users |
| Post-introduction maintenance (Operational support) | ・Support for inquiries and failures |